Yinan Yang, Electronic Commerce, Medibank Private, Canberra ACT Australia, yyang@medibank.com.au
Lawrie Brown, Australian Defense Force Academy, Canberra ACT Australia, Lawrie.Brown@adfa.edu.au.
Jan Newmarch, University of Canberra, Canberra ACT Australia, jan@ise.canberra.edu.au.
Ed Lewis, Australian Defense Force Academy, Canberra ACT Australia, e-lewis@adfa.edu.au.
W3 Trust Model, heterogeneous environment, trust value, trust attributes, transitivity of trust, Web document, trust management, Web security, scalable trust, metadata.
The major industrially adopted public key trust models are primarily hierarchically structured to form a vertically trusted environment (eg. X.509), whereas most web documents are hypertext linked to form a horizontally referral (or web-linked) environment. By introducing a set of trust attributes in such a heterogeneous environment, transitivity of trust can be implemented. The proposed Trusted W3 Model described in this paper combines a vertically trusted public key infrastructure with a horizontally referral Web classification of trust metadata.
The Internet is an important infrastructure for Electronic Commerce (E-Commerce). Health insurance, finance and commercial institutions use web documents to propagate their product information and services via the World Wide Web (W3). A survey found that "52% of Europe's financial institutions were starting to sell products online" [HREF17].
Trust has been identified as an important concern on the Web. Information technology professionals, Internet development communities, governments, and individuals continue to develop and define a trusted E-Commerce environment. From different perspectives, there are some works have looked at the issues of Trust, such as the theory of Trust [HREF14], legal aspects of Trust [McCullagh98], IT security industry viewing Trust [HREF12], and Web professional viewing Trust [HREF13]. Some Trust related projects include the DSig project [HREF13], and the REFEREE Project [HERF15] by W3C working groups.
In E-Commerce, Trust is associated with the concept of risk: risk of fraud, financial loss caused by deliberate misinformation, and misuse of personal information (eg. credit card number). As a result of these risks, there is an increasing awareness among web users of the issue of authenticity: of business partners, service providers and product information. The trustworthiness of a web document is an increasing factor affecting the rate of growth of E-Commerce.
Trust management provides an infrastructure to achieve certain levels of trust in Internet relationships. There are several public key infrastructure (PKI) trust models (X.509, PGP, SDSI/SPKI) that have been developed and implemented on the Internet today, which involve digital signatures and other security services (eg. authentication, authorisation, access-control-list, privacy). The major industrially adopted PKI trust models are primarily hierarchically structured (eg. X.509) to form a vertically trusted environment (refer section 2.1).
In contrast to the hierarchical PKI trust model, most web documents are hypertext linked to form a horizontally (or web) referral environment. The nature of web documents requires an additional way to propagate trust from a parent (or root) web document to their signed or unsigned offspring web documents, giving rise to a heterogeneous trust environment on the Internet. There are a number of methods and metadata models, such as Dublin Core (DC) [HREF4], Meta Content Framework (MCF) [HREF1], RSACI [HREF11], and Back-propagation [Marchiori98].
Existing metadata models are targeted to a particular group. For example, Dublin Core is a set of descriptors to describe web publications, the meaning of each descriptor defined from the point of view of library communities. They are "loosely defined", incomplete, and still under development [HREF16]. RSACI is used by parents and teachers for filtering the content of information on the Web. The back-propagation method [Marchiori98] tries to automatically generate a metadata description, and make it easier to classify web information by "fuzzifying" the metadata attributes. In his mathematical formula, there is a "fading factor" during the back-propagation. However, the "fading factor" has not been specifically identified nor how the "fading factor" relates to the metadatum of web documents. The DSig project uses "digitally signed labels to make authenticateable assertions about standalone documents or about manifests of aggregate objects".
There is a lack of connection and analysis on the following areas:
This paper proposes a Trusted W3 Model in an attempt to narrow the gap/disconnection between a hierarchical-trust PKI environment and a horizontally referral environment. By introducing a set of Trust Attributes (Trust metadata) and combining a vertically trusted Public Key Infrastructure (PKI) with a horizontally referral Web classification, we believe that it can provide an adequate trust environment and promote the transitivity of trust within its defined trust domain (ie. a manageable number of nodes on the Internet).
The following sections analyse both the heterogeneous environment in which the Trusted W3 Model resides, and issues of Transitivity of Trust within the heterogeneous trust web environment.
The trustworthiness of web information is a first barrier for web users considering a purchase. In other words, web users would like to have some assurance as to the trustworthiness of a web document, and the level of web security. This includes security of the communication, authentication, authorisation, anti-spoofing, legitimacy of the web business, non-repudiation and privacy, and the authenticity of web information.
Some security concerns (mentioned above) can be addressed directly by PKI trust model [HREF8] [HREF9]. However, the trustworthiness of web documents can be addressed using web classifications mechanism, metadata of trust. In other words, a properly defined set of Trust Attributes can provide information about different aspects of a web object (eg. a web document) within the heterogeneous web environment.
We will discuss the hierarchical PKI and the horizontally referral environments in turn.
Public-key cryptography has been used for number of security services, including for anti-spoofing, authentication, authorisation, non-repudiation, and secure data communications. For example, when you purchase a book via the Web, the Secure Socket Layer (SSL) can be used to create a secure session for exchanging purchase information between the server and the client.
Digitally signed certificates are also used in PKI trust models [HREF8], providing a way for authenticating parties to establish a trust relationship. The use of public key certificates is becoming an important technical mechanism for different trust models to verify the authenticity of the identity of a person, or an organisation, or a server on the Internet. Different levels of assurance are offered according to different certification policies, which provide a legal binding between a certificate authority and its subordinates. Most certificates are identity-based, which require a globally distinct name, such as an email address, the URL of a server (which contains DNS information), social security number, or ACN (for Australian business companies).
A variety of applications use certificates to protect personal email, E-Commerce gateways, web sites, securing connection and authenticity of publications on the Internet. For example, industrially well-accepted Certificate Authorities (CA) have issued Secure Server IDs as a token of trust, which ensures web users some degree of trustworthiness of the server. The server ID has a legal binding between the issuing CA and the service provider, and ensures that the server is globally unique (using the URL of the server) to provide secure communications between the server and web users through the Secure Socket Layer (SSL). The token (icon) is displayed on the screen when users access the server; web users can verify the server by clicking the icon to get information about the server. So web users are assured the business they are dealing with is legitimate and authentic.
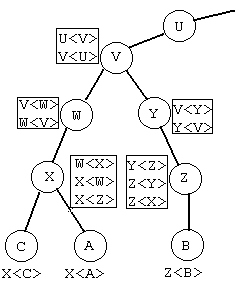
In a hierarchical certification path, a "root" CA issues certificates to its subordinate CAs and these CAs issue certificates to their subordinate CAs and so on. The "root" CA is regarded as the most trustworthy in the hierarchical certification path and every subordinate must know the root CA's public key. Any subordinate's certificate may be verified by following the certification path till the verifier reaches the root CA (eg. a common trusted CA or the CA who issued the subordinate's certificate).

(Figure1 [ITU-T96])
"A<X>,X<W>" means W signed the certificate of X, and X signed the certificate of A, where W, X, A are certificate authorities. In X.509 PKI, it is important to know that the level of trust provided by certificates "A<X>,X<W>" is the same as "A<X>". In other words, possession of "A<X>,X<W>" provides the same capability as "A<W>" (ie. A<X>,X<W> =A<W>) [ITU-T96]. It just might be a bit too optimistic to assume that there is a constant weight of trust along the arbitrary length of chain of certificates (refer section 2.1.2).
By using the digital signature certificate, scalable trust on the Internet can be achieved. Scalable trust allows a certain level of trust to travel to a large number of nodes (or entities) and still be able to maintain a maximum level of trust during its travel in a specific time frame. This way of transferring trust is called the Transitivity of Trust. Different trust models focus on different aspects of trust relationship, such as parties, scales of trust relationships and trust infrastructures. The transitivity of trust has been addressed in different ways by different trust models [HREF8].
The structure of the chain of trust forms a hierarchy environment. Trust in a PKI hierarchical-trusted environment is transferred along a set of certificates that provides a chain of trust. The chain of certificates can be of arbitrary length. To establish a trust between two entities, the verifier carries out the process of verifying the signatures on a chain of certificates until reaching the certificate that the verifier trusts. Transitivity of trust is achieved via the hierarchical chain of certificates.
Each node (CA) is an operationally independent organisation with its own human resources. CAs are bound by a mutual agreement (ie. CA policies) before issuing to its subordinates or being issued a certificate by its superior.
However, there are some factors regarding a CA’s organisational structure, operational functions, and its resources (both human and non-human resources). For example, organisational budgeting problems, frequent organisational restructures, personnel movements, outsourcing of functions, and feelings of uncertainty by employees, might affect the continuity of normal workflow, responsibilities and quality of services within organisations. These factors need to be considered in weighing the level of Trust for each node and determining how Trust can be traveled from one to another. Any factors which might reduce the weight of Trust when propagating Trust in a hierarchical environment are defined as fading factors. These factors include:
In other words, these fading factors might loosen the binding between CAs. It might be reasonable to assume that each node in the hierarchical tree structure should have a different value of trust. As we know, a "root" CA is the most trustworthy in the trust hierarchy and is regarded as having the highest trust value. Consequently, the bottom of the leaf node of the trust tree might have the least trustworthiness. All nodes in between should have appropriate trust value according their positions in the hierarchy with effect of some fading factors. These factors might also affect the trust attributes definitions and overall trust value of a web object.
In contrast to the PKI vertically trusted environment, horizontally referred web documents are the most common in a web environment. The following figure shows that common web referrals are arbitrary and horizontal (ie. web-linked).
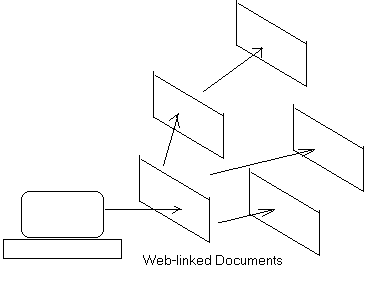
(Figure 2)
Is a certified server with Secure Server ID sufficient for web users to trust the information and make a purchase on the web? A certified server (ie. Secure Server ID) only proves the authenticity of the server (eg. web server), but does not prove web information which is contained on the server. And in most cases, the communications between the server and client are not secure until web users agree to give their credit card numbers. A well-known CA displayed the following information on its web site:
"Keep in mind that it is not necessary to make all the pages on your server secure. SSL (Secure Socket Layer) imposes some performance overhead. Therefore, most server software packages allow you to apply SSL selectively to those pages which require encryption (eg. payment pages) while leaving other pages (eg. product information pages) unsecured."
Trust has been established at the point of purchase once web users accept the trustworthiness of the web document, and are convinced either that there are no risks present or that assurances outweigh the risks.
The certified server and the web information should be considered as separate entities. An authentic server only shows web users that it (eg. the URL of the web server) is truly the server it claims it is. The CA certified the server does not provide a complete guarantee of the web information it contains, ie. the CA of the server has no total control over what web information is put on the server and who has control of the web information in operational aspects. This is particularly true when an organisation does not run its own web server (ie. outsources its web server to an other company).
What is the alternative ?
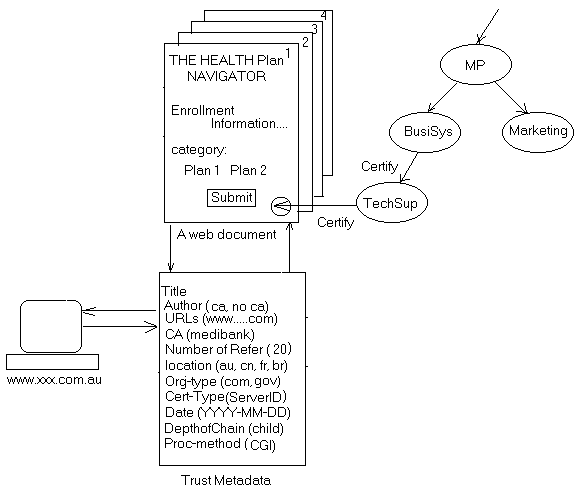
Trust information is metadata. Metadata is a simple way of providing information about a web resource, eg. a web document. The main function of the Trust Metadata (ie. a set of Trust Attributes) is to specify information on the trustworthiness of a web document, providing the Trust Attributes ( covering different aspects of a web document) have been defined properly, ie. sufficient information has to be extracted from all aspects of a web document in the heterogeneous Web environment.
Trust metadata can be simple or complicated depending on how we would like to define it. "Trust is in the eye of the beholder", ie. different beliefs and cultures may lead to different sets of trust attributes.
In simple terms, to trust a web object (eg. a web document) is similar to developing trust in strangers. We want to know about their past, present, their associates, and the environment they live in by questioning themselves, referees, their families, friends, and people we trust, to see if they know about the strangers. And we hope that we ask all the right questions to each group of people and get complete, accurate answers back, which then can be processed without an error or obstacle.
On the web, the whole process of establishing trust must be done within a few seconds. Otherwise, business providers may find no one wants to do business with them. In addition, if the method of providing Trust Attributes (which form Trust Metadata) is too complicated to implement and too difficult to use, then it will deter its use. Therefore, a simple and friendly method is very important.
What Trust Attributes are needed to gather all the trust information? In principal, Trust Attributes should be able to describe most aspects of a web document and the environment in which web documents reside. The Trust metadata should assist better interpretation of individual trust attributes and provide meaningful information on the trustworthiness of a web document. There is a basic set of attributes, such as signed or unsigned web documents, and signed or unsigned servers (eg. a web server).
However, in a heterogeneous environment, there are a number of possible combinations of certification environments. The following table shows a combination of heterogeneous environments (ie. H-domain) from which the a set of Trust Attributes resides:
|
Trust Models |
Referral web document |
Domain Name |
|
|
Certified server |
signed web document |
--> |
H-domain 1 |
|
Certified server |
non-signed web document |
--> |
H-domain 2 |
|
Non-cert-server |
signed web document |
--> |
H-domain 3 |
|
Non-cert-server |
non-signed web document |
--> |
H-domain 4 |
(Table1)
Based on the Dublin Core web resource descriptors [HREF5], we suggest the following Trust Attributes be used in Trusted W3 Model to describe a web document from the Trust perspective. The objective of Trust Attributes is to provide information about not only the contents of a web document, but also ownership, and certification information. Trust Attributes can be categorised into three groups as follows.
a. Web Object Content:
b. Relationship Between the Web Object and its Owner:
c. Relationships Between the Web Object and the CA:
However, these proposed Trust Attributes are tentative. Some refinements will be needed to enhance the Trust metadata of a web document and to reflect any changes of the heterogeneous Web environment. There may be more attributes that could be added to this initial set of trust metadata, eg. a number of different URLs refer to the web document or a number of visitors, which may provide some information about web documents that are trusted by many other web users.
Transitivity of Trust is an important concept for a Trusted Web environment. It allows a certain level of trust to travel to a defined number of nodes (ie. domain). The trust metadata is a mechanism of Transitivity of Trust. A web document has a number of dynamic links (or references) to other web documents and sites. Web documents themselves may be structured (linked) as web or hierarchical structures within a PKI trust model (either web or hierarchical structure, eg. Figure 3).
(Figure 3)
Consideration should be given to Transitivity of Trust between different web documents. Each web document may consist of one or more web pages with a uniform URL, subject, and authorship. For example, the web document " www.xxx.edu.au/" is considered to be a different web document than " www.xxx.edu.au/~yany/". In other words, they do not have the same attributes of Author, Description, Subject, and URL, although have the same DNS information. These two web-linked documents might reside on different servers, maintained by different people. Therefore, the Trust metadata may need to be re-assessed and re-evaluated when changes occur to web documents.
Each trust attribute of a web document may or may not be the same when one web document refers to another. Based on their definitions, some attributes are transferable along with its trust value (eg. if the same Author writes different web documents, which are linked, the weight trust of the attribute of Author remains the same). Some may not be transferable along with its trust value (eg. two web documents should not have the same Identifier). Some may be partially transferable (eg. a web document may be certified, which is also linked to a non-certified web document, but with the same Subject) although its trust value may reduce according to its conditions.
When one web document refers to another web document (ie. two web-linked documents), we need to consider issues of transferability of web document attributes. This is the time to re-assess and re-evaluate the trustworthiness of a newly referred web document by its parent web document. We denote "Y" for transferable attribute values, "N" for non-transferable attribute values, and "P" for partially transferable values.
There are some conditions or situations which prevent or promote the retention of the weight of trust for each attribute:
Note: More examples on transferability of each attribute will be given in subsequent papers.
The following table summarises the proposed Trust Attributes and their transferability.
|
a. Description of content |
Value |
Transferable between documents |
|
1. Title |
eg. name of resource |
Y/N |
|
2. Subject |
eg. keywords, phrases |
Y/N/P |
|
3. Keywords |
eg. health insurance |
Y/N/P |
|
4. Description |
eg. textual description |
Y/N/P |
|
5. Coverage |
eg. applied for au only |
Y/N/P |
|
6. Category |
eg. News, finance |
Y/N/P |
|
7. Location |
eg. URL, DNS |
Y/N/P |
|
8. Identifier |
position of the referral tree |
N |
|
9. Source |
point to original form |
Y/N |
|
10. Language |
eg. French, English |
Y/N |
|
11. Create-Date |
eg. yyyy-mm-dd |
Y/N |
|
12. Proc-Method |
eg. html hard coded |
Y/N |
|
13. Rights |
eg. license agreement |
Y/N |
|
b. Relationship of web objects with its owner |
Value |
Transferable between documents |
|
1. Publisher |
eg. (co-) author, org-name |
Y/N |
|
2. Orga-Type |
eg. gov, edu, com |
Y/N |
|
3. Num-Diff-URL |
eg. refer to 10 URLs |
Y/N |
|
c. Relationship of web object & CA |
Value |
Transferable between documents |
|
1. Cert-Site |
Boolean |
Y/N |
|
2. Generation |
position in the tree |
P |
|
2. Cert-Docu |
Boolean |
Y/N |
|
3.Cert-Type |
eg. server ID, personal ID |
Y/N |
|
4. CA |
immediate superiors |
Y/N |
|
5. Root CA |
eg. Dept. |
Y/N |
|
6. Certify-Date |
eg. yyyy-mm-dd |
Y/N |
|
7. CA-Country |
eg. us, uk, au |
Y/N |
(Table2)
Note:
Y => transferable means the two web-linked web documents may have the same value of the attribute and have same weight of trust.
N=> not transferable means the two web-linked web documents have different value of the attribute and may have different weight of trust, and the ID is restricted to non-transferable attributes.
P => partially transferable means some possible "fading factors" will reduce the weight of trust on the attribute or where two web-linked documents share some information with the same attributes.
Some of the web-linked web documents may or may not be within its trust hierarchical domain (refer Table1), ie. a certified server may refer to a server which has not been certified. To be able to weigh the trust of a web document in a heterogeneous environment, we should take into account not only the horizontally referral environment, but also the hierarchical trust PKI environment.
In general, the following conclusions might be drawn:
This paper has introduced a set of Trust Attributes, described the Trust W3 Model and discussed the need to assess the value of trust within the context of the H-domains. We also discussed the reasons and philosophy behind the proposed Trusted W3 Model, and introduced preliminary discussion on the flow of Transitivity of Trust in a heterogeneous environment.
Trust is largely driven by an increased awareness of web security among web users. To address security concerns, primarily hierarchical PKI models can provide a vertically trusted environment. However, a horizontally web-linked referral environment adds another dimension in the Web environment. By introducing Trust metadata as a glue to closely join these two dimensions together, Transitivity of Trust can flow from a hierarchical trust domain to a web-linked domain to form a coherent heterogeneous Web environment, called the Trusted W3 Model.
Web service providers will benefit from the Trust W3 Model. They are now able to provide Trust information to web users, and provide assurance that their service and products are authentic and trustworthy. Web users will also benefit from the Trust W3 Model: they are now able to make more informed decisions on who they want to do business with, based on assurances of the authenticity of services, service-providers, and products.
For future work, we will propose realistic and practical methods of calculating the numerical result of trust value based on the Trust W3 Model. If the web information is highly important, then the trust-value would be dynamically calculated on the access link each time. In other words, high trust-value not only represents trust but also indirectly reflects the importance of the information (eg. purchasing goods). For web users who are concerned with Trust and Security on the Internet, they will be able to see the trust indicator on the web browser where trust-value can be displayed.
[Josang99] Audun Josang, "An Algebra for Assessing Trust in Certification Chains", proceeding of the 1999 Network and Distributed System Security (NDSS) Symposium.
[Marchiori98] Massimo Marchiori, "The limits of Web metadata, and beyond", The World Wide Web Consortium (W3C), MIT Laboratory for Computer Science, 545 Technology Square, Cambridge, MA 02139, USA.
[ITU-T96] ITU-T Recommendation X.509, "Information Technology – Open Systems Interconnection – the Directory: Authentication Framework". International Telecommunication Union, 1996.
[McCullagh98] A. McCullagh, "E-Commerce – A Matter of Trust", the Proceedings of the Information Industry Outlook Conference, Canberra, 7 November 1998.
Yinan Yang, Lawrie Brown, Jan Newmarch, and Ed Lewis, © 1999. The authors assign to Southern Cross University and other educational and non-profit institutions a non-exclusive licence to use this document for personal use and in courses of instruction provided that the article is used in full and this copyright statement is reproduced. The author also grants a non-exclusive licence to Southern Cross University to publish this document in full on the World Wide Web and on CD-ROM and in printed form with the conference papers and for the document to be published on mirrors on the World Wide Web.