- Dr Lawrie Brown
- Australian Defence Force Academy
- crypto algs essential for security
- brief overview of block ciphers
- AES call for new standard alg
- LOKI97 candidate
- some final thoughts
- private (single, shared) key algs
- fast, good for bulk data encryption
- block vs stream ciphers
- public (two) key algs
- key validation & distribution, slower
- digital signature schemes
- sign & authenticate data, public key
- hash functions
- compress data to fixed size to sign
- will consider block ciphers
- fixed sized input (64,128 bits)
- fixed sized key (56,64,128,256 bits)
- need mode of use for arbitrary data
- ECB, CBC, CFB, OFB
- use an easily reversed structure for decryption (feistel structure)
- DES - 56 key/64 data / 16 round
- standardised in 1977 by ANSI/NSA
- based on earlier Lucifer design
- can now demonstrate exhaustive search for a key, cf RSA DSI contest
- also theoretically broken by both differential & linear cryptanalysis
- faster than exhaustive search, but ...
- FEAL - 64-128/64/4-32+
- NTT Japan, 1987
- a number of attacks known
- IDEA - 128/64/8
- Lai/Massey, 1990
- widely used in PGP, SSH; patented
- LOKI - 64/64/16
- Australian (ADFA), 1989/91
- reasonably secure, unencumbered
- Differential Cryptanalysis
- attack ciphers using relationships between pairs of encryptions with known input & observed output diffs
- Linear Cryptanalysis
- attack ciphers using (near) linear relationships between selected input, output, key bits
- Related Key Attacks
- attack using relations between keys
- Blowfish - 128+/64/16, Schneier 94
- bulk data, slow keying
- CAST - 64/64/8, Canadian 93
- appln specific boxes, used in Canada
- RC2/RC5 - vary key/data/rounds
- RSADSI proprietary, widely licenced
- SAFER - 64-12 / 64 / 6+, Massey 94
- TEA - 128 / 64 / 32 - simple, v. fast
- IJCE Timing Encryption (1MByte) Key Init
- Algorithm Time (ms) Rate (Kbps) 1000 (ms)
- --------- --------- ----------- --------
- Blowfish 13592 617 46536
- CAST5 15023 558 665
- DES 26208 320 279
- TripleDES 86904 96 971
- IDEA 24696 339 408
- LOKI91 15681 534 61
- LOKI97 (+) 42340 198 1878
- RC2 24073 348 553
- RC4 (*) 8113 1033 1267
- SAFER 34566 242 1323
- Square 18580 451 1061
- clear DES needs replacement for commercial (esp banking) & govt
- needs to secure info well into next century (60 yrs+ archival)
- so US NIST has issued AES call for
- private key symmetric block cipher
- announced Sept 97, submit by Jun 98
- 2 phases public evaluation
- will select 1 cipher at end for standard
- private key symmetric block cipher
- 128-bit data, 128/192/256-bit keys
- stronger & faster than Triple-DES
- full specification & design details
- both C & Java implementations
- NIST committed to public release of submissions & unclass analyses
- soliciting analyses from public
- after 1st phase will shortlist ~5
- currently 16 expressions of interest
- but names not released by NIST yet
- know LOKI97, Pentagon
- LOKI97 is
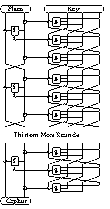
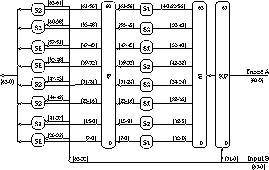
- private key feistel S-P block cipher
- 128-bit data
- 256-bit key schedule initialised from 128, 192, 256-bit keys
- 16 round data computation using a complex highly non-linear function
- two layers of S-P per round
- same function also used in key schedule
- key escrow is dead
- key backup is useful for orgs
- for archival & recovery, not comms
- 40-bit keys are manifestly insecure
- 75+ is recommended minimum
- need CA's now
- need strong encryption now
- brief overview of block ciphers
- past
- cryptanalyses
- AES call
- new LOKI97 cipher
- some other thoughts
Lawrie.Brown@adfa.edu.au / 05-May-98